You are a network support specialist for CiscoSims, an IT training firm. They have just installed a new router(R1) in to their network. The router was successfully installed and is passing traffic. However, your manager is concerned about security and has tasked you with implementing access security for the new router R1.
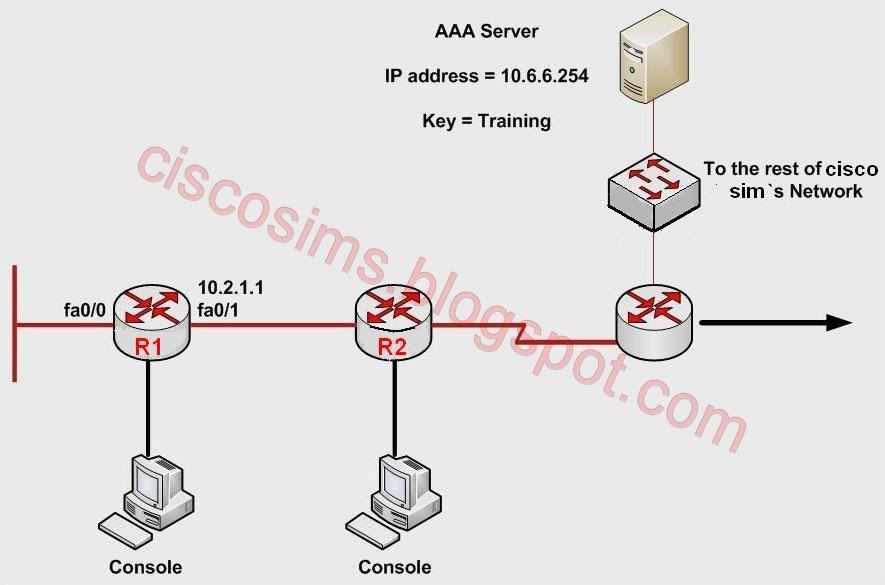
The portion of CiscoSims's security policy related to router access states:-
# The default user access authentication scheme requires that the user be authenticated using the router's local database.
# User console access should be authenticated using the default authentication scheme.
# User aux port access should be authenticated using the default authentication scheme.
# User Vty access should be protected via a password that is validated using only the corporate Tacacs server.
For this router installation:-
# The corporate Tacacs server has an IP address of 10.6.6.254 and uses a shared key of Training.
# The enable password for R1 is Go2en
You have successfully completed your task when you have verified that you can login into:
# Rl's console using the local user's ID of BDnet1 with a password of Wer#1
# R2's console using the username of BDnet2 with a password of Wer#1 and establish a SSH session from R2 to R1 using the test Tacacs user's ID of cisco with a password of cisco123
Configuration Solution:
R1>enable
R1#conf t
Enable the TACACS server in R1 :-
R1(config)#aaa new-model
Configure the Tacacs server ip address- 10.6.6.254 and share key Training :-
R1(config)#tacacs-server host 10.6.6.254 key Training
Configure user authentication using router's local database :-
R1(config)#aaa authentication login default local
Configuration to validate vty access using Tacacs server :-
R1(config)#aaa authentication login vty group tacacs+
Configure console and Aux ports for default authentication :-
R1(config)#line console 0
R1(config-line)#login authentication default
R1(config)#line aux 0
R1(config-line)#login authentication default
Configure VTY for TACACS server authentication :-
R1(config)#line vty 0 15
R1(config-line)#login authentication vty
R1(config)#exit
R1#copy run start
Now login to R2 with provided credentials to establish ssh session with R1 :-
R2#ssh -l cisco 10.2.1.1
The session should be successfully establish with the test Tacacs user's ID of cisco and password of cisco123
...............................................................................................................................




do we need to add transport input ssh when configuring vty 0 15 line in order to ssh from router 2?? or aaa automatically convert vty access to allow ssh sessions?
ReplyDeleteWe don't need "transport input ssh" command, coz the vty access is validated using tacacs server and he'll take care of it.
ReplyDeletewhere you configure the user and the password cisco 123??
ReplyDelete# And the user BDnet1 with a password of Wer#1??
# And the user BDnet2 with a password of Wer#1??
@ above poster
ReplyDeleteUsername and passwords are pre-configured on the routers. We don't need to configure them.
is incompleted configureation for AAA
ReplyDeletewhy u not add the username BDnet1 password Wer#1 after aaa newmodel
ReplyDeletecan u get me the explainaton of last portion of tacas server simulation
ReplyDelete