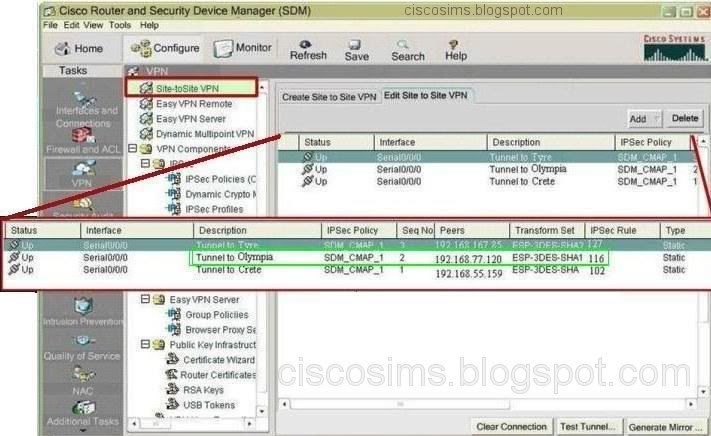
Q1. You work as a network engineer at CiscoSims. Which defined peer IP address and local subnet belong to Crete? (Choose two.)
A. peer address 192.168.55.159
B. peer address 192.168.77.120
C. peer address 192.168.167.85
D. subnet 10.5.15.0/24
E. subnet 10.8.28.0/24
F. subnet 10.5.33.0/24
Explanations:-
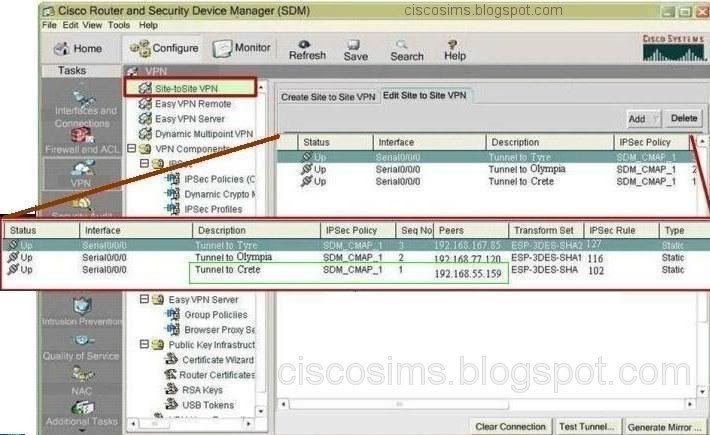
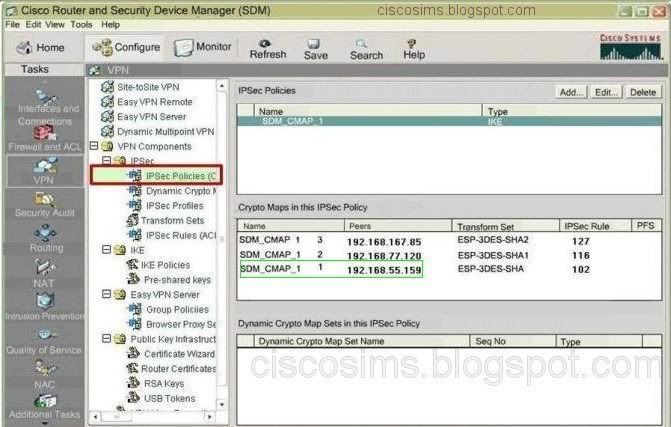
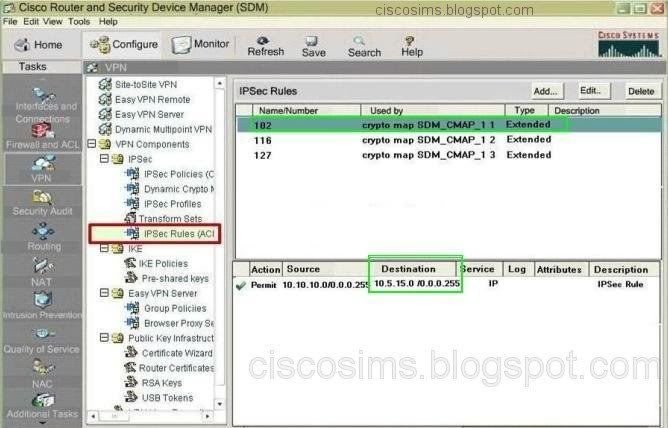
After login the SDM headquarters, VPN->site-to-site VPN, find the configuration in view of Crete branch, and we can see the status (UP), the interface S0/0/0, the IPSEC policy (SDM_CMAP 1), peer (192.168.55.159), Transform sets (ESP-3DES-SHA), ipsec policy (1602), etc. The further step is to find the option of ipsec policies from VPN components. We can see the detailed information of 102. The ACL only allows 10.10.10.0/24 to access all the IP services of 10.5.15.0/24.
.................................................................................................................................................
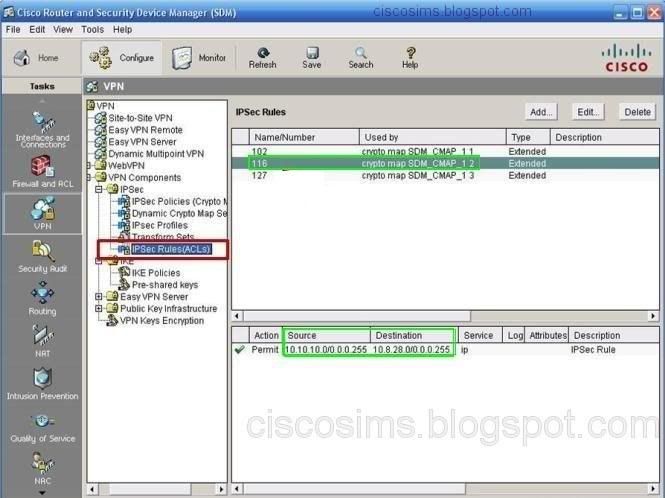
Q2. Internet Protocol Security (IPsec) is a suite of protocols for securing Internet Protocol (IP) communications. Which IPSec rule is used for the Olympia branch and what does it define? (Choose two.)
A. 127
B. 116
C. 102
D. IP traffic sourced from 10.10.10.0/24 destined to 10.5.15.0/24 will use the VPN.
E. IP traffic sourced from 10.10.10.0/24 destined to 10.8.28.0/24 will use the VPN.
F. IP traffic sourced from 10.10.10.0/24 destined to 10.5.33.0/24 will use the VPN.
Explanations:
After login the headquarters SDM, VPN->site-to-site VPN, find the configuration in view of Olympia branch, and we can see the status (UP), the interface S0/0/0, the IPSEC policy (SDM_CMAP 1), peer (192.168.77.120), Transform sets (ESP-3DES-SHA 1), ipsec policy (116), etc. The further step is to find the ipsec rule option from VPN components. We can see the detailed information of 116. The ACL only allows 10.10.10.0/24 to access all the IP services of 10.8.28.0/24.
..............................................................................................................................................................
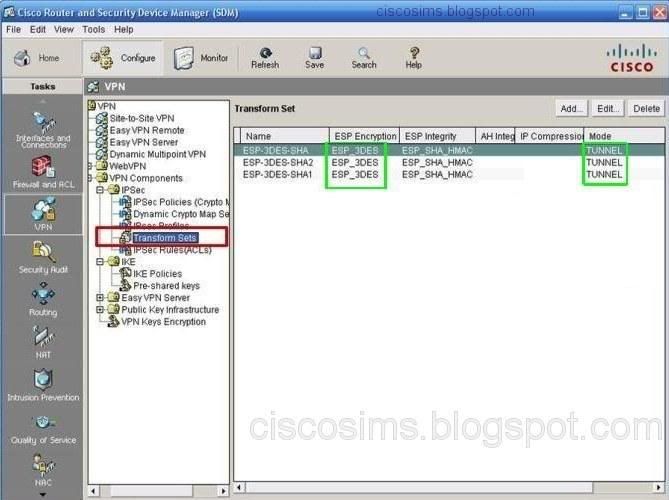
Q3. Which algorithm as defined by the transform set is used to provide data confidentiality when connected to Tyre?
A. ESP-3DES-SHA
B. ESP-3DES-SHA1
C. ESP-3DES-SHA2
D. ESP-3DES
E. ESP-SHA-HMAC
Explanations:-
So as to check the VPN configuration information, open the SDM and find the Tranform sets from VPN->VPN components. It is possible to view the applied encryption method is using ESP-3DES.
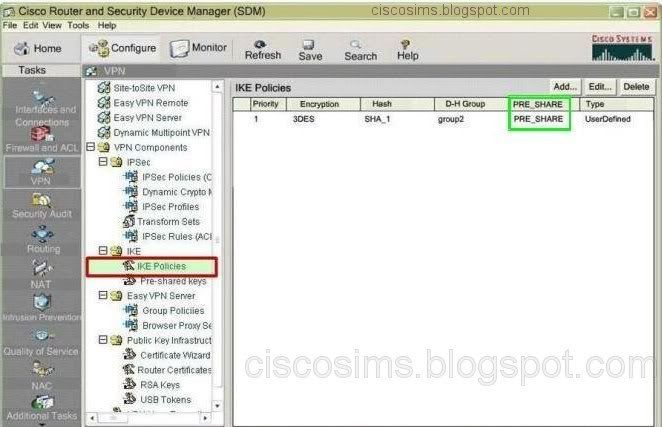
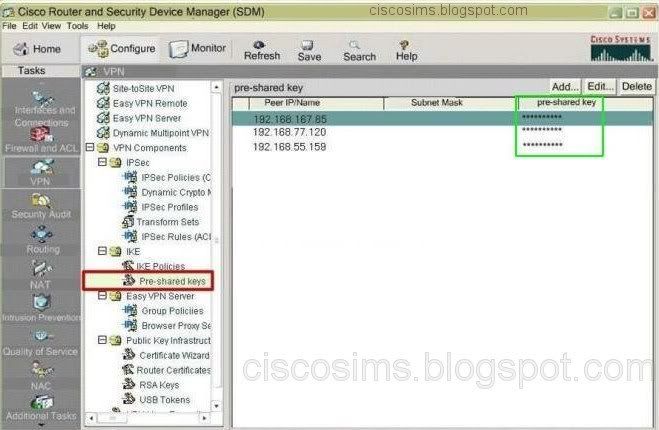
Q4. You are a network engineer at CiscoSims, can you tell me which peer authentication method and which IPSEC mode is used to connect to the branch locations? (Choose two.)
A. Transport Mode
B. Tunnel Mode
C. Digital Certificate
D. Pre-Shared Key
E. GRE/IPSEC Transport Mode
F. GRE/IPSEC Tunnel Mode
Explanations:-
So as to check the VPN configuration information, open the SDM and find the IKE policies from VPN->VPN components. It is possible to view that the authentication method is using PRE_SHARE, that is, Pre-Shared Key. Select VPN->VPN components to find Tranform sets, and it is possible to view the applied transmission mode is tunnel. So we choose BD.
 ............................................................................................................................................
............................................................................................................................................




Good works.Thanks a BUNCH !!!!!!!!!!
ReplyDeleteI work as a chat support for a mobile company. Every now and then I get not-so-nice chats. How do i get their IP so I can report or block them? Your response will be highly appreciated. Thank you in advance!
ReplyDeletevpn