CiscoSims Industry is a large worldwide sailing charter. The company has recently upgraded its Internet connectivity. As a recent addition to the network engineering team, your task is with documenting the active Firewall configurations on the CiscoSims router using the Cisco Router and Security Device Manager (SDM) utility.
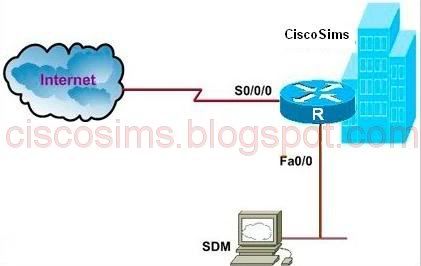
Using the SDM output from Firewall and ACL Tasks under the Configure tab, answer the following questions:
Q1. Which statement is correct?
A. Both FastEthernet 0/0 and Serial 0/0/0 are trusted interface.
B. Both FastEthernet 0/0 and Serial 0/0/0 are untrusted interface.
C. FastEthernet 0/0 is a trusted interface and Serial 0/0/0 is an untrusted interface.
D. FastEthernet 0/0 is an untrusted interface and Serial 0/0/0 is a trusted interface.
Explanations:-
An untrusted interface (connecting to the Internet) is an interface that is configured to receive messages from outside of the network or firewall. A trusted interface is one that is configured to receive only messages from within the network.
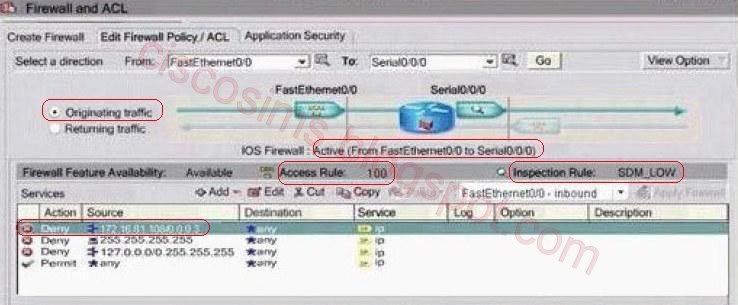
The direction of ACL100 is from F0/0 to S0/0/0, which allows all the access of source IP addresses except 172.16.81.108/0.0.0.3, 255.255.255.255, 127.0.0.0/8. So it might be the direction from inside to outside network. The direction of ACL101 is from S0/0/0 to F0/0, which only allows the echo-reply/icmp, time-exceede, unreachable services of the destination address of 172.16.81.108, denies 0.0.0.0 / 8, 10.0.0.0/8, 127.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16, 224.0.0.0/ 4, and 240.0.0.0/ 4, as well as adds log to any access. So it might be the direction from outside to inside network.
Therefore, F0/0 is used to connect the inside network and S0/0/0 is used to connect the outside network.
.......................................................................................................................................
Q2. Which two statements would specify a permissible incoming TCP packet on a trusted interface in this configuration? (Choose two.)
A. The packet has a source address of 10.79.233.107
B. The pocket has a source address of 172.16.81.108
C. The packet has a source address of 198.133.219.40
D. The destination address is not specified within the inspection rule SDM_LOW.
Explanations:-
Because the interface is configured with CBAC firewall, when the data arrives at this interface, the router will first inspect the state table, if the table has the item corresponding to the data, then the router will forward the data according to the state table, if not, the router will use ACL to inspect the data. The secure interface ACL must permit data due to not creating the state table. So A and C are correct.

The direction of ACL100 is from F0/0 to S0/0/0, which allows all the access of source IP addresses except 172.16.81.108/30, 255.255.255.255, 127.0.0.0/8. So it might be the direction from inside to outside network. If TCP data packets are allowed, then it is impossible to match. So, the source address cannot be 172.16.81.108.
....................................................................................................................................
Q3. Which two options would be correct for a permissible incoming TCP packet on an untrusted Interface in this configuration? (Choose two.)
A. The packet has a source address of 10.79.233.186
B. The packet has a source address of 172.16.81.108
C. The packet has a source address of 198.133.219.135
D. The session originated from an untrusted interface
E. The session originated from a trusted Interface
Explanations:-
According to the question, after configuring CBAC, the TCP traffic on the untrusted interface can be divided into two types:
1. The inspected return traffic from the intranet is permitted by the state table, so C is right.
2. The TCP traffic permitted by the ACL comes from external network, so E is right.
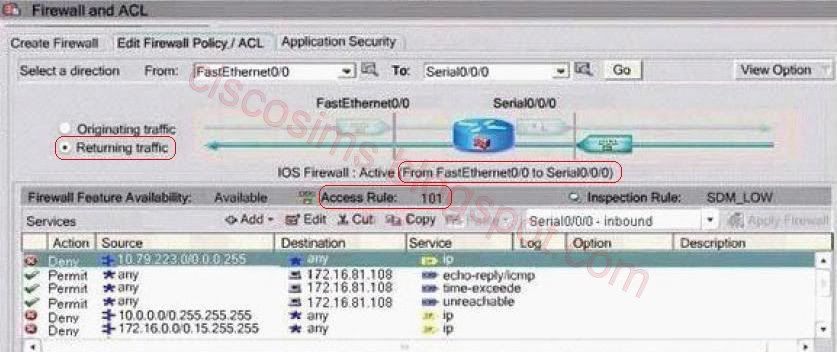
The direction of ACL101 is from S0/0/0 to f0/0, which only allows the echo- reply/ icmp, time-exceede, unreachable services of the destination address of 172.16.81.108, denies any IP data packets from 0.0.0.0/8, 10.0.0.0/8, 127.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16, 224.0.0.0/4, 240.0.0.0/4 and 10.79.223/24, as well as adds log to any access. As to the address 172.16.81.108, only part of the ICMP packets are allowed. The address 198.133.219.135 is first initiated from the inside network. If an address of 198.133.219.135 is received from the outside network it should be directely dropped.
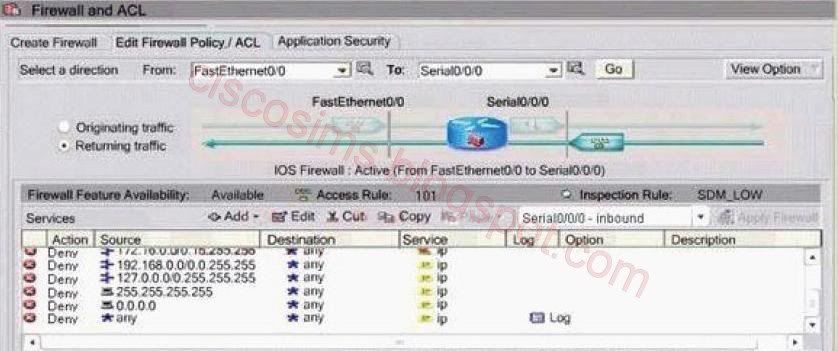
......................................................................................................................................




Hi. I get Q1 and Q2, but I cant get to agree with Q3.
ReplyDeleteThe final rule on the FW is deny any - this is where I get confused. This is for return traffic to the inside, not originating traffic from the outside. Originatiign from the outside should be deny, but surely it should be allow when it's return from the outside?
Thanks all :)
The Traffic can be any type, and icmp is a kind of traffic, so if the source traffic is 198.133.219.135 and is pinging 172.16.81.108,
ReplyDeleteThere will be echo-reply